References
- Sites
- Books
- Cryptography
- Authentication
- Network
- YouTube
- Web
- Softwares
- Passwords
- Operation Systems
- Virtual Machines for Pentest
- DataBases
- CLI Commands
- Search Engines
- Browsers
- Frameworks Docs
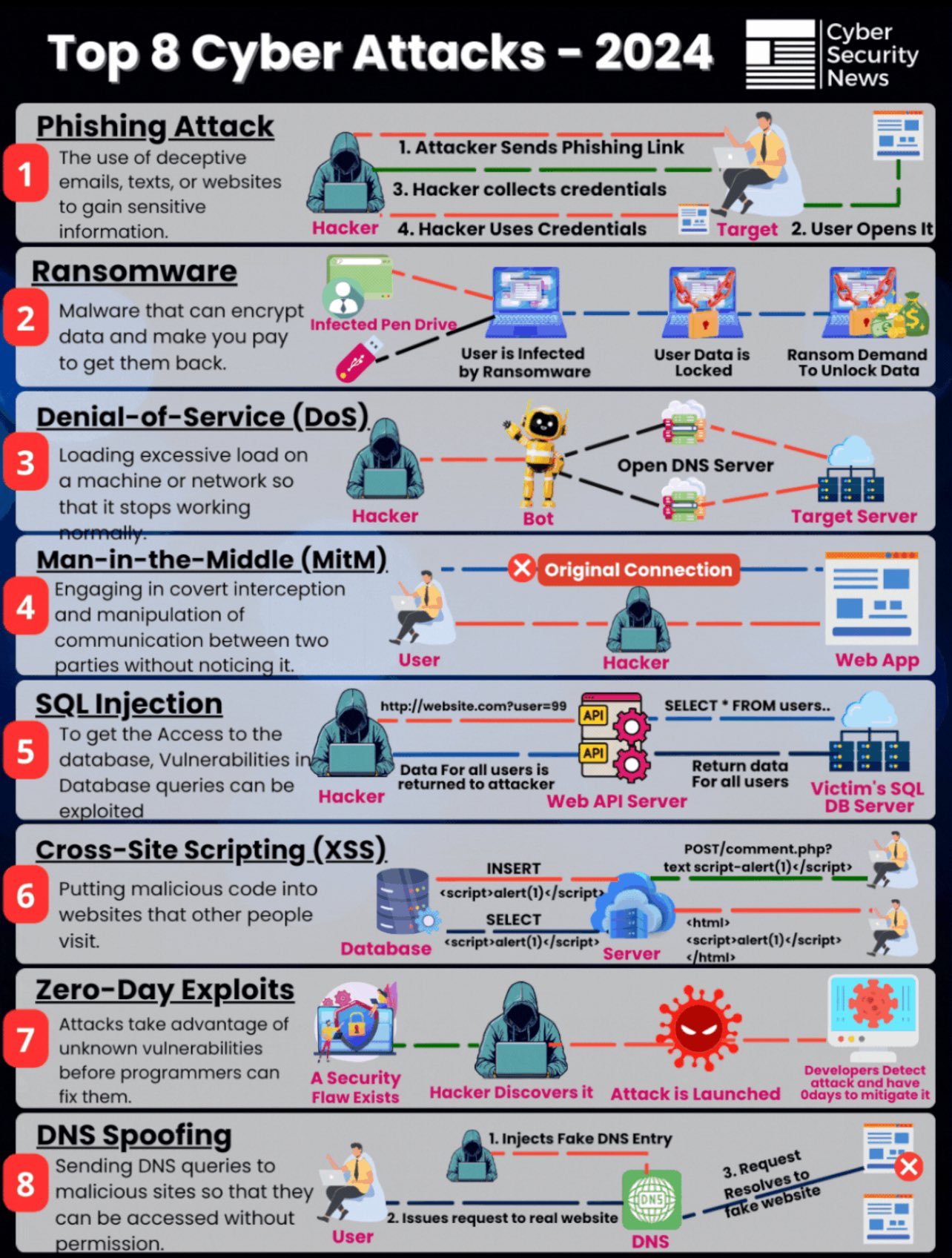
HTTPS
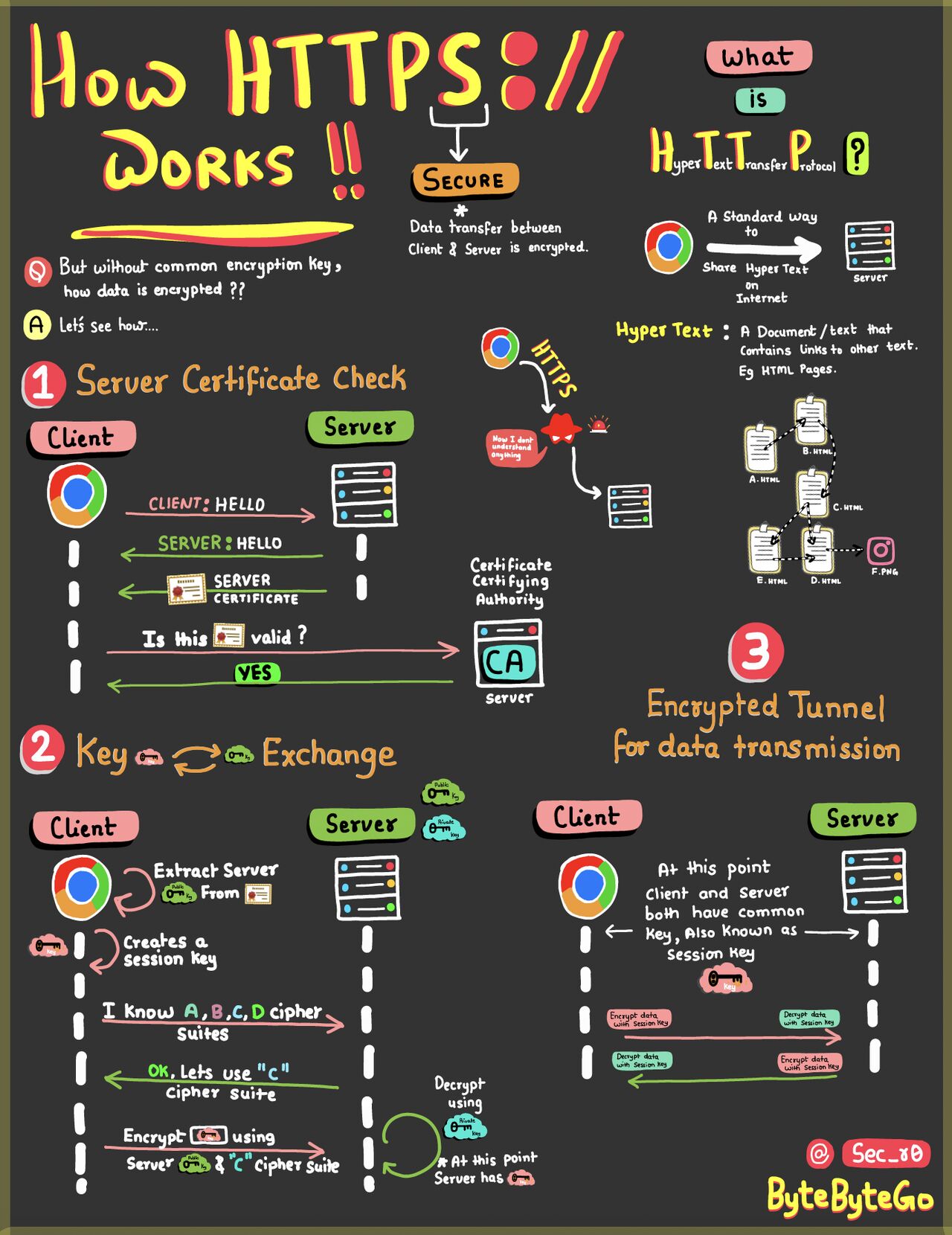
Authentication
Hashing vs Encryption
Hashing and encryption are fundamental techniques in software security, but they have different purposes and characteristics. Here are the main differences between them, along with some use cases:
Hashing
Purpose:
- Hashing is used to ensure data integrity and verify authenticity without having to revert the data to its original state.
Characteristics:
- Irreversibility: Hashing is a one-way process; once data is hashed, it cannot be reverted to its original state.
- Fixed Length: Regardless of the size of the input data, the resulting hash value will have a fixed size.
- Collisions: Ideally, hash functions are designed to minimize collisions (when two different sets of data produce the same hash), but they cannot be completely eliminated.
Use Cases:
-
Integrity Verification: Hashes are used to verify that data has not been altered. For example, when downloading a file, the hash of the downloaded file can be compared with the published hash to ensure that the file has not been corrupted.
-
Password Storage: Instead of storing passwords directly, systems store the hash of passwords. When a user attempts to log in, the system compares the hash of the provided password with the stored hash.
-
Digital Signatures: Hashes are used in combination with encryption to create digital signatures, ensuring that the content has not been altered and authenticating the source.
Encryption
Purpose: - Encryption is used to protect the confidentiality of data by ensuring that only authorized parties can access the information.
Features:
-
Reversibility: Encryption is a two-way process; encrypted data can be reverted to its original state through decryption using an appropriate key. 2. Key: Cryptographic security relies on a key that must be kept secret. Cryptography can be symmetric (same key for encryption and decryption) or asymmetric (different keys for encryption and decryption).
-
Complexity: Cryptography tends to be more computationally complex than hashing, due to the need to encrypt and decrypt data.
Use Cases:
-
Secure Data Transmission: Encryption is used to protect data transmitted over the internet, such as in HTTPS connections, ensuring that sensitive information (such as banking details) cannot be intercepted and read by unauthorized parties.
-
Sensitive Data Storage: Sensitive data, such as medical records or financial information, is encrypted to protect privacy and ensure that only authorized users can access it. 3. Authentication and Identity: Authentication systems, such as smart cards or security tokens, use cryptography to securely verify the identity of users.
Summary of Differences
| Feature | Hashing | Encryption |
|---|---|---|
| Purpose | Integrity | Confidentiality |
| Irreversibility | Yes | No |
| Fixed Length | Yes | No |
| Use of Keys | No | Yes |
| Computational Complexity | Lower | Higher |
| Use Cases | Integrity checking, password storage, digital signatures | Secure transmission, secure storage, authentication |
These differences show that hashing and encryption are complementary, each meeting specific security needs within software systems.
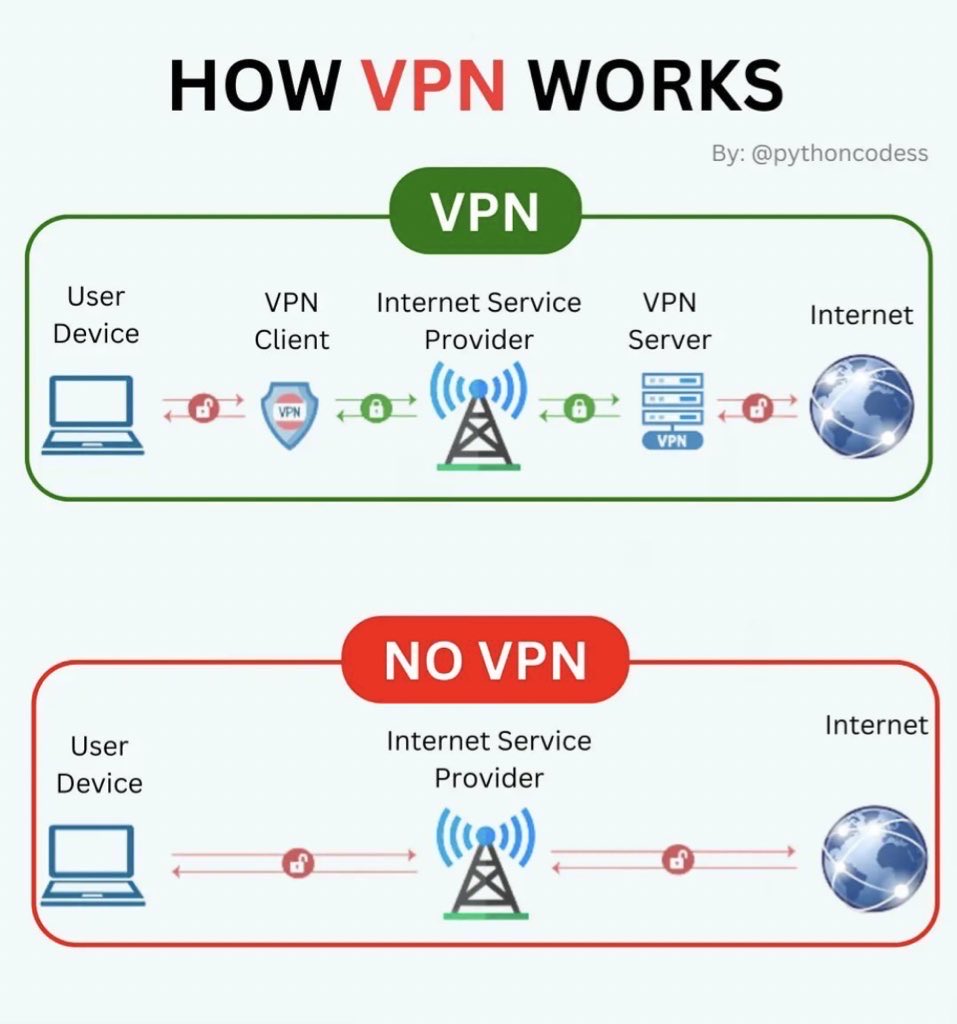
VPN - Virtual Private Network
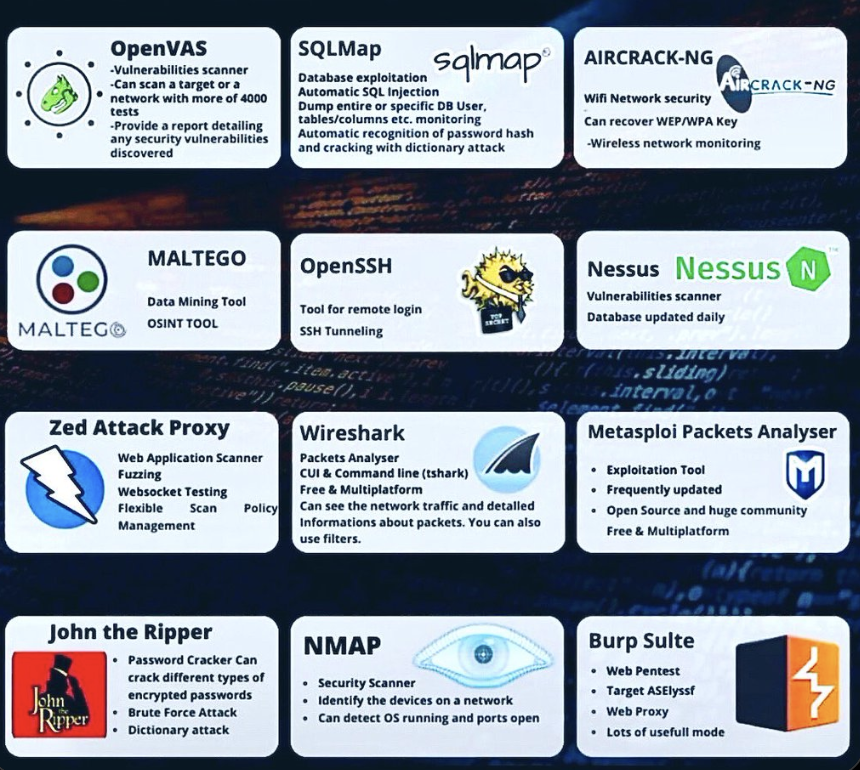
Tools
Attacks